I/INTRO
hMailServer is a free e-mail server for Microsoft Windows. It's used by Internet service providers, companies, governments, schools and enthusiasts in all parts of the world.
It supports the common e-mail protocols (IMAP, SMTP and POP3) and can easily be integrated with many existing web mail systems. It has flexible score-based spam protection and can attach to your virus scanner to scan all incoming and outgoing email.
prefer:
http://www.hmailserver.com/II/Functionality1/Services(POP3,STMP,IMAP)
2/database support(
Microsoft SQL Server,
PostgreSQL and
MySQL)
3/webmail(you can use Roundcube,SquirrelMail ,AfterLogic WebMail Pro)
4/Security(hMailServer is pre-configured to have high security when it comes to relaying and authentication so that no one can use your server to send spam messages. It also supports the very popular open source virus scanner ClamAV. Configuring hMailServer to use ClamAV only takes a single click! The server also supports black list servers and other spam-stopping mechanisms such as SPF and MX lookups).
5/feature
* POP3, SMTP, IMAP
* Virtual domains
* Built-in backup
* SSL encryption
* Anti-spam
* Anti-virus
* Scripting
* Server-side rules
* Multilingual
* Routing
* MX backup
* Multihoming
* SQL backend
* Web administration
* ClamWin
* SpamAssassin
6/other(hMailServer can use account of Active directory)
III/INSTALL Step 1:download hmail server from
http://www.hmailserver.com/index.php?page=download
Step 2:Install hmail server (it auto install)
Step 3: After install add domain(conheotiensinh.co.cc)
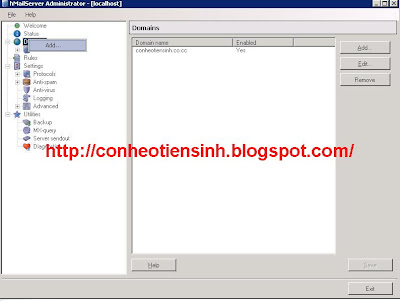
Step 4:Add Account you can use account of AD
Step 5:install web admin and Web mail
For easier install you can use xampp(http://www.apachefriends.org/en/xampp.html)
1/Web admin
- Copy folder PHPWebAdmin from in folder install hmailServer to folder htdocs of xampp
-Set the value of rooturl to the URL where the WebAdmin will be accessed.
Example:
$hmail_config['rooturl'] = "http://localhost/PHWebAdmin/"; 
2/Webmail
a/use SquirrelMail
Download It from (http://www.squirrelmail.org/download.php).In your mail folder, you will found a
config folder with a file named
config_default.php. Rename the
config_default.php to
config.php.Edit it
$domain = "localhost"; $smtpServerAddress = "localhost"; // your hMailServer address $imapServerAddress = "localhost"; // your hMailServer address $imap_server_type = "hmailserver";$data_dir = "C:/xampp/htdocs/mail/data/";
$attachment_dir = "C:/xampp/htdocs/mail/attach/"
b/Use roundcube(recommend)
-Download from
http://roundcube.net/ -Create database roundcubemail from phpmyadmin
-Rename your “
db.inc.php.dist” to “
db.inc.php” and “
main.inc.php.dist” to
“main.inc.php” in folder config of roundcube
-Edit your “
db.inc.php” and change this line
“$rcmail_config['db_dsnw'] = ‘mysql://roundcube:pass@localhost/roundcubemail’;” with this “
$rcmail_config['db_dsnw'] = ‘mysql://root:@localhost/roundcubemail’;”
-access
http://localhost/roundcubemail/installer and configure it
c/use AfterLogic WebMail Pro(not recommend Buy Liscense)
- Download from http://www.afterlogic.com/
-Access http://your_webmail_web_address/adminpanel/install.htm you will install it auto


















